Tag: Internet
How to Disagree
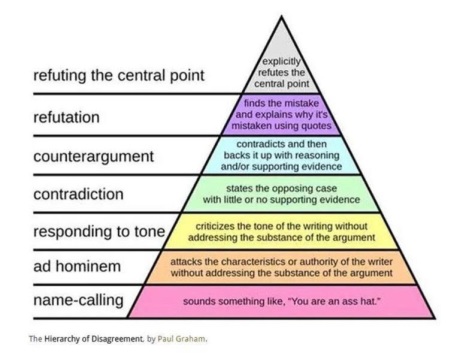 If we’re all going to be disagreeing more, we should be careful to do it well. What does it mean to disagree well? Most readers can tell the difference between mere name-calling and a carefully reasoned refutation, but I think it would help to put names on the intermediate stages. So here’s an attempt at a disagreement hierarchy:
If we’re all going to be disagreeing more, we should be careful to do it well. What does it mean to disagree well? Most readers can tell the difference between mere name-calling and a carefully reasoned refutation, but I think it would help to put names on the intermediate stages. So here’s an attempt at a disagreement hierarchy:
Source: How to Disagree
New Anti-Censorship Tool Marionette Could Make it Easier to Slip Past China’s Great Firewall | MIT Technology Review
 Governments can now block anticensorship tools such as the Tor anonymity network or encrypted VPN connections, for example. But a new censorship evasion tool called Marionette may help reverse that trend. Marionette helps Internet traffic that would normally be blocked masquerade as ordinary, permitted online behavior. It can be configured to make your activity emulate just about any type of “innocent” activity, such as online gaming or Skype, by analyzing samples of that kind of traffic. Marionette can even be programmed to respond in the right way to maintain its cover if actively probed by a censorship computer system, a tactic China sometimes uses to investigate suspicious connections before blocking them.
Governments can now block anticensorship tools such as the Tor anonymity network or encrypted VPN connections, for example. But a new censorship evasion tool called Marionette may help reverse that trend. Marionette helps Internet traffic that would normally be blocked masquerade as ordinary, permitted online behavior. It can be configured to make your activity emulate just about any type of “innocent” activity, such as online gaming or Skype, by analyzing samples of that kind of traffic. Marionette can even be programmed to respond in the right way to maintain its cover if actively probed by a censorship computer system, a tactic China sometimes uses to investigate suspicious connections before blocking them.
Coull hopes that Marionette will one day be integrated into the anonymity network Tor or the censorship evasion tool Lantern—two systems backed by the U.S. government and used by activists, government workers, and NGOs. He’s already talked with Tor developers about Marionette’s open-source code. The system was introduced in a paper at the USENIX Security conference in Washington, D.C., this month, and developed by Coull with Kevin Dyer andThomas Shrimpton of Portland State University
Net Neutrality – Be Careful What You Wish For
 When Google’s Eric Schmidt called White House officials a few weeks ago to oppose President Obama ’s demand that the Internet be regulated as a utility, they told him to buzz off. The chairman of the company that led lobbying for “net neutrality” learned the Obama plan made in its name instead micromanages the Internet.
When Google’s Eric Schmidt called White House officials a few weeks ago to oppose President Obama ’s demand that the Internet be regulated as a utility, they told him to buzz off. The chairman of the company that led lobbying for “net neutrality” learned the Obama plan made in its name instead micromanages the Internet.
Mr. Schmidt is not the only liberal mugged by the reality of Obamanet, approved on party lines last week by the Federal Communications Commission. The 300-plus pages of regulations remain secret, but as details leak out, liberals have joined the opposition to ending the Internet as we know it.
The Progressive Policy Institute said: “There is nothing progressive about the FCC backsliding to common carrier rules dating back to the 1930s.”
The Electronic Frontier Foundation, which supports applying the 1934 law to the Internet, nonetheless objects to a new regulation giving the FCC open-ended power to regulate the Internet. “A ‘general conduct rule,’ applied on a case-by-case basis,” the EFF wrote, “may lead to years of expensive litigation to determine the meaning of ‘harm’ (for those who can afford to engage in it).”
What if at the beginning of the Web, Washington had opted for Obamanet instead of the open Internet? Yellow Pages publishers could have invoked “harm” and “unjust and unreasonable” competition from online telephone directories. This could have strangled Alta Vista and Excite, the early leaders in search, and relegated Google to a Stanford student project. Newspapers could have lobbied against Craigslist for depriving them of classified advertising. Encyclopedia Britannica could have lobbied against Wikipedia.
Among the first targets of the FCC’s “unjust and unreasonable” test are mobile-phone contracts that offer unlimited video or music. Netflix , the biggest lobbyist for utility regulation, could be regulated for how it uses encryption to deliver its content.
What Happens in an Internet Minute?
Do you know what happens in one minute on the Internet? In just one minute, more than 204 million emails are sent. Amazon rings up about $83,000 in sales. Around 20 million photos are viewed and 3,000 uploaded on Flickr. At least 6 million Facebook pages are viewed around the world. And more than 61,000 hours of music are played on Pandora while more than 1.3 million video clips are watched on YouTube.
 Today, the number of networked devices equals the world’s population. By 2015, the number of networked devices is expected to be double the world’s population. And by the time we reach 2015, it would take five years to view all the video content crossing IP networks each second. Click Infrograph to expand.
Today, the number of networked devices equals the world’s population. By 2015, the number of networked devices is expected to be double the world’s population. And by the time we reach 2015, it would take five years to view all the video content crossing IP networks each second. Click Infrograph to expand.
China’s Next Generation
 “Prison Break” is huge in China and its star, Wentworth Miller is not only mobbed everywhere he goes in China, he’s the frickin’ face of GM on TV commercials!
“Prison Break” is huge in China and its star, Wentworth Miller is not only mobbed everywhere he goes in China, he’s the frickin’ face of GM on TV commercials!
The show has never been aired on any Chinese TV network, only on the Web.
Xi Jinping (China’s next president and in his late 50s), for example, still remembers vividly being thrown in jail as a kid as a political prisoner on his dad’s behalf during the Cultural Revolution. He’s China’s leader for the next decade, and his “Sixties’ were a bit different from the Boomers.
via Thomas P.M. Barnett’s Globlogization – Thomas P.M. Barnett’s Globlogization.
Does the Web change how we think?
” By flooding us with information, the Internet also “causes more confidence and illusions of knowledge” (Nassim Taleb of MIT, author of The Black Swan), but makes our knowledge seem “more fragile,” since “for every accepted piece of knowledge I find, there is within easy reach someone who challenges the fact” (Kevin Kelly, cofounder of Wired).
Even more intriguing are the (few) positive changes in thinking the Internet has caused. The hyperlinked Web helps us establish “connections between ideas, facts, etc.,” suggests Csikszentmihalyi. “Result: more integrated thought?” For Kelly, the uncertainty resulting from the ubiquity of facts and “antifacts” fosters “a kind of liquidity” in thinking, making it “more active, less contemplative.” Science historian George Dyson believes the Internet’s flood of information has altered the process of creativity: what once required “collecting all available fragments of information to assemble a framework of knowledge” now requires “removing or ignoring unnecessary information to reveal the shape of knowledge hidden within.” Creativity by destruction rather than assembly.
The War on Spam & Cybercrime
While Western governments debate the efficacy, or legality, of going on the offensive against Internet spies and criminals, more Internet security companies, and academic researchers, are taking the initiative. The most recent victory was the elimination of the Neustar of Lethic botnet, which represented about ten percent of all spam email sent.
The biggest victory took place in 2008, when a small ISP, McColo Corporation, was taken off line. This caused worldwide spam traffic to decline by over 50 percent in one day. Before that, two similar ISPs, the Russian Business Network and Intercage, had a less dramatic impact on spam traffic, and Internet based criminal activity in general, when they were shut down.
Internet crime, particularly spam (unsolicited email) has become a big money maker. Because of the very low cost of sending it, you need only one response for several million spam messages, to make lots of money. But the same ISPs that host the spammers, also host operations that try to sneak into business, government and personal computers to steal stuff (bank account information, trade secrets, classified military information).
Overloaded Internet
Video boom threatens to gridlock the internet | Technology | The Observer
Information meltdown
· Electricity reached one quarter of Americans 46 years after its introduction. Telephones took 35 years and televisions 26 years. In just six years, broadband reached 25 per cent penetration.
· It took two centuries to fill the shelves of the Library of Congress with more than 57 million manuscripts, 29 million books and periodicals, 12 million photographs, and more. Now, the world generates an equivalent amount of digital information nearly 100 times each day.
Internet Innovation Alliance Continue reading “Overloaded Internet”
Rash Of Internet Undersea Cables Cut
Apparently, Ships Can Drag Anchors from Egypt to Malaysia | I Love Bonnie.net
As I said: 3 was quite a few. 4 is pushing it. 5 starts to make you wonder. In case you aren’t familiar with that part of the world, here’s a map that I made which shows the approximate locations of the “cuts” in the underwater cables: 
We’re supposed to believe that these were most likely caused by an anchor from a ship fighting a storm. This author finds it hard to believe that this anchor was drug behind a boat from Egypt to Malaysia.


